A false positive is a mistake that happens occasionally — the antivirus thinks a download is harmful when it’s actually safe. But malicious people may try to trick you into downloading malware with this assurance. 2008-2018 - 0 false positives by Defender over those 10 years. 2019 - 10 or so false positives 2020 - well over 35 'false positives'. The first 'false positive' by defender was just a few days after wj32 quit working at Microsoft. Mark Russinovich sent both of us job offers but I turned it down because of work on critical issues at Electronic Arts.
Trojan Win32/Tiggre!rfn virus removal guide
What is Trojan Win32/Tiggre!rfn?
Trojan Win32/Tiggre!rfn is high-risk malware designed to perform a number of malicious tasks on victims' computers. It is also known as 'Trojan.GenericKD.12694003' (by BitDefender) and 'W32/Autoit.CGO!tr' (by Fortinet). Trojan Win32/Tiggre!rfn is distributed in various ways, including spam emails (malicious attachments), fake Adobe Flash Player updaters, malicious websites, chain infections, and even Facebook messages.
Trojan Win32/Tiggre!rfn is versatile malware, since it performs various functions depending on developers' choices. For example, it can misuse system resources to mine cryptocurrency. The entire crypto-mining process essentially based on solving various 'mathematical equations'. Mining tools employ system resources to perform calculations. Each time an 'equation' is solved, a single unit of currency (e.g., 1 Bitcoin) is mined. Since an identical 'equation' is solved by a number of computers simultaneously, the reward is split between each device depending on the power of the device and how much work is performed. All revenue is received by cyber criminals (crypto wallet), whilst users receive nothing in return. In fact, all this is done without their consent, and since mining takes up to 100% of computer resources, systems often become unstable and virtually unusable. Furthermore, within certain circumstances (high room temperatures, poor cooling systems, etc.) hardware can be damaged (components might overheat). Trojan Win32/Tiggre!rfn also gathers various data, including saved logins/passwords, keystrokes, banking information, and so on. Collected data is often misused to generate revenue. Therefore, the presence of malware such as Trojan Win32/Tiggre!rfn might lead to serious financial and privacy issues (e.g., cyber criminals can transfer funds to their accounts, purchase illegal items under your name, and so on).
In some cases, Trojan Win32/Tiggre!rfn infiltrates systems along with a number of adware-type applications. These programs are not as harmful as Trojan Win32/Tiggre!rfn, but can be frustrating and problematic. Potentially unwanted adware-type programs (PUPs) typically deliver intrusive advertisements and gather sensitive data. Intrusive ads conceal underlying website content (thereby significantly diminishing the browsing experience), and also redirect to malicious sites and even run scripts that stealthily download and install malware. Clicking these ads can lead to malicious sites. Furthermore, adware gathers IP addresses, URLs visited, search queries, pages viewed, and other data relating to browsing activity. Collected information is shared with third parties (potentially, cyber criminals). Therefore, adware poses a threat to your privacy and Internet browsing safety. For these reasons, all adware-type PUPs must be eliminated immediately.
| Name | Trojan Win32/Tiggre!rfn malware |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Detection Names | Avast (Win32:TrojanX-gen [Trj]), BitDefender (Trojan.GenericKD.41401183), ESET-NOD32 (A Variant Of Win32/Kryptik.GUFO), Kaspersky (Backdoor.Win32.Androm.srmx), Full List (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) | To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Malwarebytes. |
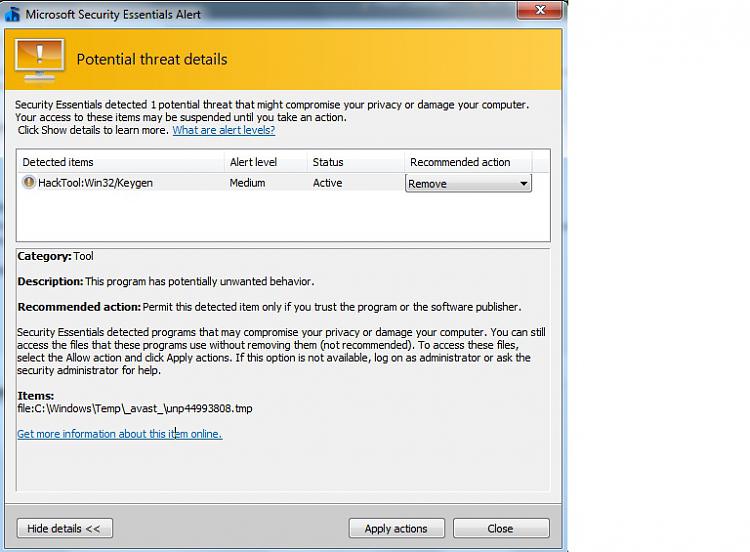
Hacktool Win32 Keygen False Positive Coronavirus
Trojan Win32/Tiggre!rfn is very similar to Pony, TrickBot, and FormBook. In fact, there are dozens of viruses that also gather information, mine cryptocurrencies, and perform other malicious tasks. Adware-type apps share many similarities. By offering 'useful features', PUPs attempt to give the impression of legitimacy, however, rather than enabling the functions promised, adware poses a direct threat to your privacy and Internet browsing safety. The only purpose of this software is to help developers generate passive revenue.
How did Trojan Win32/Tiggre!rfn infect my computer?
As mentioned above, Trojan Win32/Tiggre!rfn is promoted using spam emails, fake Flash Player updaters, and Facebook. Spam emails contain malicious attachments (e.g., MS Office documents, JavaScript files, etc.) that, once opened, stealthily download and install malware. Fake updaters claim that the player is outdated (although it is not) and encourage users to renew it. Rather than updating the player, however, these tools download and install Trojan Win32/Tiggre!rfn. Criminals also proliferate this malware via malicious sites that, once opened, execute scripts designed to download and install Trojan Win32/Tiggre!rfn without consent. Another method is 'chain-infecting': a computer is infected with malware that proliferates other viruses (in this case, Trojan Win32/Tiggre!rfn). Developers also use scripts that send spam messages on Facebook. The message simply contains a video file, however, this is a disguise - rather than opening the video, the user will open a AutoIt script that will infect the system.
How to avoid installation of malware?
The main reasons for computer infections are poor knowledge and careless behavior. The key to safety is caution. Therefore, pay close attention when browsing the Internet. Think twice before opening files/links received via email, Facebook accounts, Skype, and so on. If files/links seem irrelevant or have been sent from suspicious/unrecognizable names/email addresses, delete these messages immediately and certainly do not open attached files/links. Furthermore, keep installed applications up-to-date and remember that criminals proliferate malware via fake updaters. Therefore, apps should be renewed using implemented update features or tools provided by the official developers only. Having a reputable anti-virus/anti-spyware suite installed and running is also paramount. If you believe that your computer is infected with Trojan Win32/Tiggre!rfn, we recommend running a scan with Malwarebytes for Windows to automatically eliminate infiltrated malware.
Instant automatic malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Malwarebytes is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD MalwarebytesBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Malwarebytes. 14 days free trial available.
Quick menu:

Hacktool Win32 Keygen Reddit
- STEP 1. Manual removal of Trojan Win32/Tiggre!rfn malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task, usually it's better to let antivirus or anti-malware programs do it automatically. To remove this malware we recommend using Malwarebytes for Windows. If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here's an example of a suspicious program running on user's computer:
If you checked the list of programs running on your computer, for example using task manager and identified a program that looks suspicious you should continue with these steps:
Download a program called Autoruns. This program shows auto-start applications, Registry and file system locations:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in 'Safe Mode with Networking':

Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened 'General PC Settings' window, select Advanced startup. Click the 'Restart now' button. Your computer will now restart into the 'Advanced Startup options menu'. Click the 'Troubleshoot' button, and then click the 'Advanced options' button. In the advanced option screen, click 'Startup settings'. Click the 'Restart' button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in 'Safe Mode with Networking':
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click 'Restart' while holding 'Shift' button on your keyboard. In the 'choose an option' window click on the 'Troubleshoot', next select 'Advanced options'. In the advanced options menu select 'Startup Settings' and click on the 'Restart' button. In the following window you should click the 'F5' button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in 'Safe Mode with Networking':
Extract the downloaded archive and run Autoruns.exe file.

In the Autoruns application click 'Options' at the top and uncheck 'Hide Empty Locations' and 'Hide Windows Entries' options. After this procedure click the 'Refresh' icon.
Check the list provided by Autoruns application and locate the malware file that you want to eliminate.
You should write down it full path and name. Note that some malware hides their process names under legitimate Windows process names. At this stage it's very important to avoid removing system files. After you locate he suspicious program you want to remove right click your mouse over it's name and choose 'Delete'
After removing the malware through Autoruns application (this ensures that the malware won't run automatically on the next system startup) you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the file of the malware be sure to remove it.
Reboot your computer in normal mode. Following these steps should help remove any malware from your computer. Note that manual threat removal requires advanced computer skills, it's recommended to leave malware removal to antivirus and anti-malware programs. These steps might not work with advanced malware infections. As always it's better to avoid getting infected that try to remove malware afterwards. To keep your computer safe be sure to install latest operating system updates and use antivirus software.
To be sure your computer is free of malware infections we recommend scanning it with Malwarebytes for Windows.
